Summary of Kubernetes Disaster Recovery Concepts and Best Practices
Let’s start with a summary of the core concepts covered in this article.| Concept | Description |
| The imperative nature of disaster recovery in Kubernetes | Disaster recovery in Kubernetes is crucial due to its complex dynamic nature. Potential risks like human errors, security breaches, and software bugs require a comprehensive strategy to mitigate data loss, service disruption, and compliance violations. |
| Real-life use cases | Covering essential use cases for disaster recovery in Kubernetes, including protection from ransomware attacks and managing cloud infrastructure outages. Key features like immutable backups and standard format backups (QCOW2) are crucial for ransomware protection, while a comprehensive disaster recovery strategy is vital for tackling infrastructure or hardware failures. |
| Laying out a Kubernetes disaster recovery plan | Creating a production-grade disaster recovery plan for Kubernetes requires application-centric backups, pre-staged backups, and policy-based automation to ensure seamless recovery across diverse disaster scenarios. |
| Best practice | Description |
| Test and validate | Regularly test your backup and recovery processes by simulating disaster scenarios to minimize real-world disruption. |
| Automate | Embed DR practices into existing orchestration tools, simplifying management and enhancing infrastructure resilience. |
| Store backups off-site | Ensure backups are stored off-site or in a separate environment to safeguard against localized disasters. |
| Use backup policies | Implement policy-driven backup and recovery workflows to guarantee consistent, reliable backups without manual intervention. |
| Select an application backup strategy | Application-consistent backups ensure data integrity at precise moments, which is essential for transactional applications backed by databases. Application-centric backups capture everything—data, configs, operators, and dependencies—making them ideal for intricate Kubernetes environments. |
| Implement an event-driven disaster recovery | Leverage a tool like Event-Driven Ansible (more on this later) for automated incident response, triggering timely recoveries to remote clusters. |
The imperative nature of disaster recovery in Kubernetes
Kubernetes enables scalability and efficiency but brings complexity that poses significant challenges in disaster recovery. This section highlights a few real-life scenarios and potential risks to underscore the importance of DR in Kubernetes clusters.General scenarios emphasizing the importance of DR
- Application downtime due to human error: Even seasoned engineers can make mistakes, like erroneous deletions or misconfigurations. In Kubernetes, these mistakes can propagate rapidly, crippling multiple containers and services across the system and causing extended application downtime that can have severe operational and financial repercussions.
- Security breaches: Kubernetes environments are attractive targets for cyber-attacks due to their often complex and dynamic nature. A breach can lead to data compromise or service disruption, making it imperative to have a DR plan that includes rapid isolation and recovery steps to minimize damage.
- Infrastructure failures: Hardware malfunctions, network issues, or software glitches in the underlying infrastructure can result in data loss or service downtime. Given Kubernetes’ distributed architecture, the impact of such failures can be amplified, disrupting multiple services and necessitating a quick and effective DR response.
- Software bugs and problematic updates: Upgrades and patches are routine in Kubernetes environments. However, these can sometimes introduce unforeseen bugs that destabilize services. A robust DR strategy enables quick rollback to a stable state, minimizing service disruption and maintaining system integrity.
Potential risks and impacts on Kubernetes clusters
- Data loss: Accidental deletion or corruption of persistent data is a critical risk in Kubernetes, particularly for stateful applications. This loss can disrupt operations and lead to significant recovery efforts, underscoring the need for regular and reliable backups.
- Service disruption: Kubernetes orchestrates a wide array of services. If not quickly contained and resolved, a failure in one area can lead to a domino effect, causing widespread outages and severely impacting business operations.
- Compliance violations: Data breaches or losses can have legal implications for businesses in regulated sectors, leading to fines and sanctions.
- Reputation damage: Frequent downtime or data breaches can tarnish an organization’s reputation, eroding customer trust and loyalty. This reputational impact can have long-term consequences on business prospects and growth.
- Increased complexity in recovery: Kubernetes’s distributed and dynamic nature adds complexity to disaster recovery. Identifying the root cause and restoring services requires navigating a maze of dependencies and interactions, making a streamlined DR process essential.
Automated Kubernetes Data Protection & Intelligent Recovery
Perform secure application-centric backups of containers, VMs, helm & operators
Use pre-staged snapshots to instantly test, transform, and restore during recovery
Scale with fully automated policy-driven backup-and-restore workflows
Real-life use cases
Here, we explore a few use cases where disaster recovery is essential in Kubernetes. These scenarios reflect common and significant issues that Kubernetes administrators and engineers often encounter.
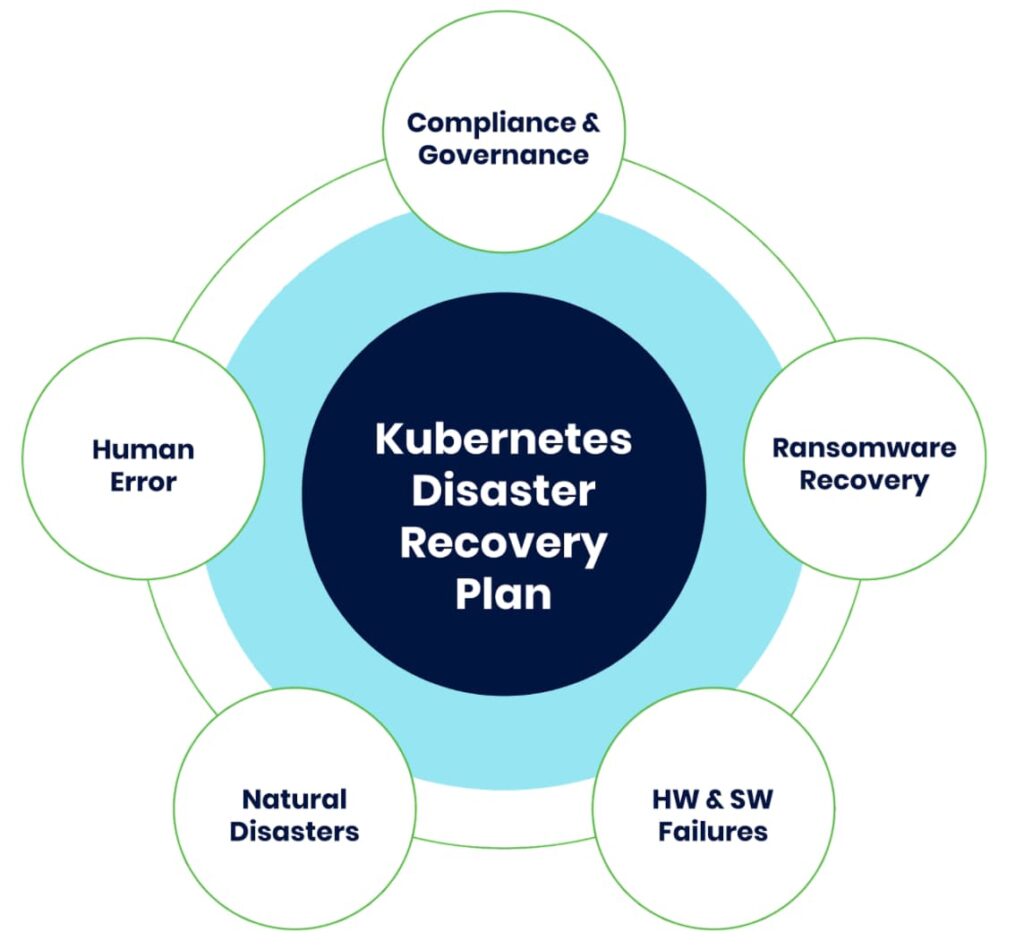
The use cases for having a Kubernetes disaster recovery plan (source: Trilio)
Kubernetes ransomware protection
In the face of rising cyber threats, particularly ransomware, Kubernetes environments demand robust protection. According to some estimates, ransomware attacks have increased as much as 13%, with an average cost of around 1.85 million and an average downtime of 22 days, highlighting the growing threat landscape.
A comprehensive disaster recovery tool or strategy should encompass several vital aspects for counteracting ransomware threats in Kubernetes environments:
- Immutable backups: Integration with backup repositories like S3-supported storage is essential for creating “object-locked” backups. This feature ensures that backups remain unaltered, providing immunity against ransomware modifications.
- 360° application protection: A strategy aligned with the NIST Cybersecurity Framework is necessary for complete protection, covering everything from identifying vulnerabilities to recovering applications. To bridge together multiple tools, your backups should be in a standard format such as QCOW2.
- Rapid recovery: The ability to quickly restore operations is crucial. Easy, one-click workflows facilitate quick recovery, significantly diminishing the likelihood and impact of ransomware attacks. This includes reducing the need to consider paying for ransomware.
Trilio is well-equipped to address these crucial aspects of ransomware protection in Kubernetes. It supports immutable backups, uses the QCOW2 image format for easier integration with security scanning tools, and enables rapid recovery of your data. Its full suite of features and capabilities aligns with best practices, offering a robust solution for maintaining the integrity and availability of applications in the face of cyber threats.
Watch this 1-min video to see how easily you can recover K8s, VMs, and containers
Kubernetes cloud infrastructure outages
Infrastructure or hardware failures, though infrequent in today’s cloud Kubernetes environments, can have severe consequences when they occur. This use case addresses the critical role of the disaster recovery process in Kubernetes environments, particularly in the context of infrastructure or hardware failures. In Kubernetes environments, infrastructure or hardware failures present distinct challenges:- Amplified Impact Due to Interconnected Services: In Kubernetes, the failure of critical infrastructure components can trigger widespread system disruptions. Given the platform’s reliance on a mesh of interconnected services and applications, a single point of failure can lead to cascading effects, impacting a range of services and applications beyond the initial failure point.
- Complex Recovery Requirements: Production Kubernetes environments are often complex, with multiple layers of configurations, services, and dependencies. Recovering from a hardware failure is not just about restoring data; it involves re-establishing network configurations, service connections, and various application dependencies. This complexity requires a detailed and well-coordinated recovery process to ensure all components are correctly reinstated.
- Heightened Risk for Critical Operations: Many businesses rely on Kubernetes for their critical operations and applications, making infrastructure outages a significant risk to vital operations and potentially leading to service-level agreement (SLA) violations.
Laying out your Kubernetes disaster recovery plan
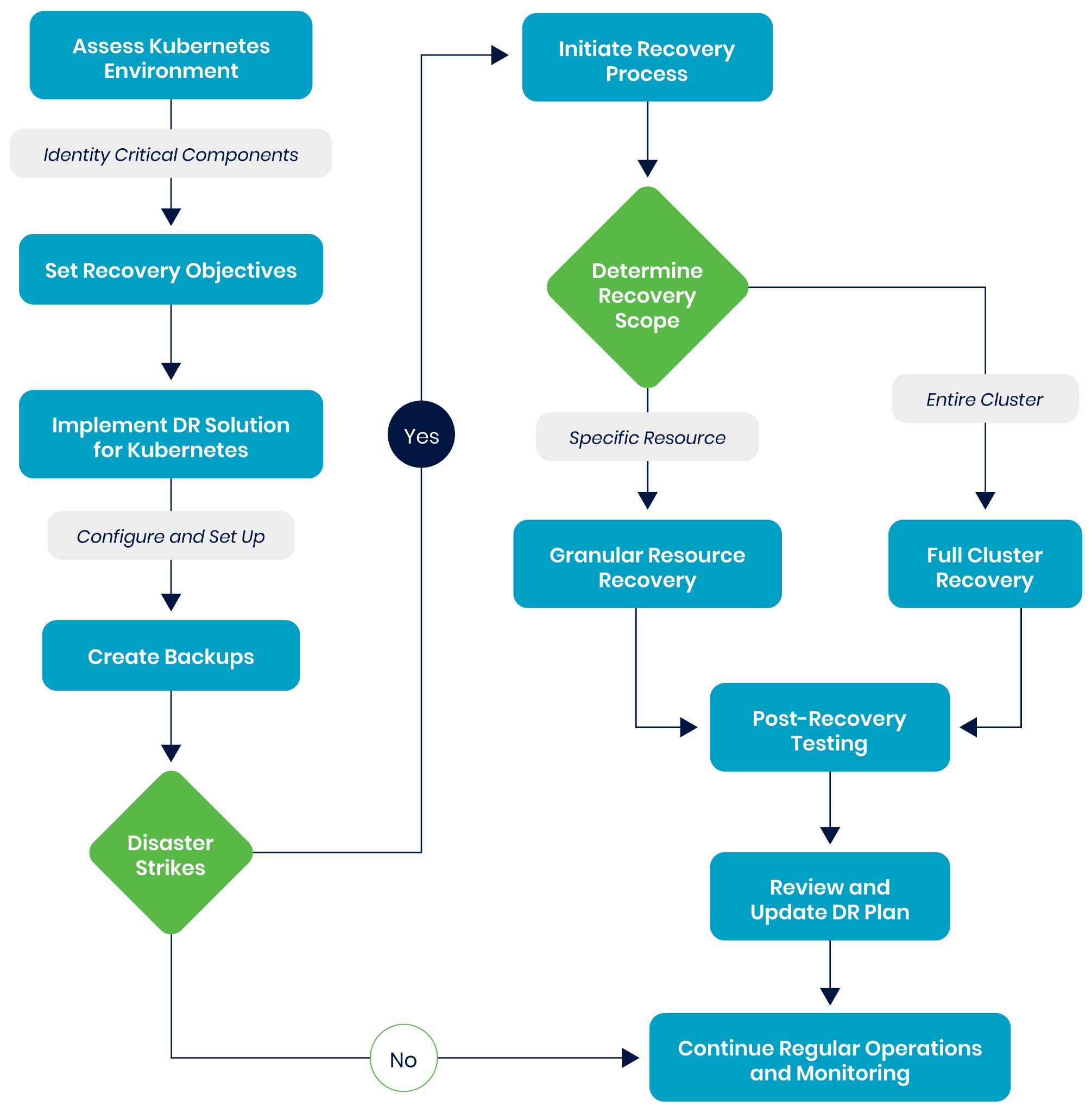
Developing a disaster recovery plan for Kubernetes can be complex. A well-structured plan should incorporate various DR methods, such as cold and warm standby, and allow the administrator to restore components based on criticality. This section will explore the technical steps in creating a production-grade DR plan.1. Assess and plan your backup requirements
- Identify critical components: Begin by auditing your Kubernetes environment. Pinpoint deployments, services, persistent volumes, and essential configurations. This identification process is crucial to understanding what needs to be included in the backups. Set recovery objectives: Define a clear recovery time objective (RTO) and recovery point objective (RPO). The RTO determines the maximum acceptable time your environment can be offline. The RPO refers to how much recent data you can afford to lose in case of disruption while resuming normal operations. One way to reduce RTO is to identify which components are the most critical to be restored first.
2. Implement granular recovery strategies
- Granular recovery options: Plan for scenarios requiring the recovery of specific elements of your cluster, like the ability to restore individual resources, such as particular pods, deployments, or persistent volumes, providing flexibility in handling various disaster scenarios.
- Restore testing: Regularly test granular restores to ensure that specific components can be recovered quickly and accurately without restoring entire applications or clusters. To simplify testing your restores, consider integration with automation and orchestration tools. We look into how to do this later in this article under Best Practices.
3. Set up multi-cloud and cross-cluster migrations
- Plan for warm-standby scenarios: Set up continuous data replication to a secondary, ready-to-go cluster if your strategy involves maintaining a warm-standby environment. This setup is handy for critical applications requiring high availability and minimal downtime.
- Replication configuration: Fine-tune the replication settings. Decide on the replication frequency, which will balance how current the data needs to be and the resources available for replication processes. Ensure the network bandwidth and storage resources are adequate for the replication load.
4. Regularly test and validate backup and recovery processes
- Conduct DR drills: Periodically simulate disaster scenarios to test the efficacy of backup integrity and recovery processes. This includes practicing the restoration of backups in a test environment to validate the recovery time against your RTO.
- Monitor and adjust: Utilize monitoring tools to track the performance of your backups. Adjust your DR strategies based on these insights and any changes in your Kubernetes environment or business requirements. A widely used and recommended way to monitor these metrics is through the Prometheus exporter and integration with Grafana. You can learn more about this through reading on how Trilio does observability with Prometheus and Grafana.
5. Document your DR plan
- Maintain clear documentation: Keep a comprehensive record of your DR strategy. This documentation should include detailed procedures for initiating backups, steps for recovery, and how to handle different disaster scenarios.
- Update as necessary: Regularly review and revise your documentation to stay current with your operational environment and DR strategies. This includes updating it for changes in your Kubernetes setup, configurations, or backup storage targets.
Best practices for Kubernetes disaster recovery
Here are a few best practices you should consider when developing a robust disaster recovery strategy for Kubernetes.Learn about the features that power Trilio’s intelligent backup and restore
Regularly test backup and recovery processes
To ensure your DR plan’s efficacy, frequently simulate various disaster scenarios, like accidental deletions or resource misconfigurations. These accidental deletions might be as minor yet disastrous as deleting a production cluster instead of a testing cluster because the clusters have a similar name.
Automate DR processes
Integrate with orchestration tools like Ansible Automation Platform for enhanced DR capabilities. This integration facilitates the easy management of DR processes, even for junior admins or beginners, and promotes a more resilient infrastructure.
Keep backups off-site or in a separate cluster or environment.
Diversify the location of your backups to mitigate the risks associated with site-specific disasters. This could involve storing backups in a geographically separate data center, cloud storage, or a different Kubernetes cluster. Such geographical distribution of backups is a crucial strategy in protecting against regional outages, natural disasters, and site-specific failures.
Securing backups in Kubernetes: application-consistent and application-centric approaches
- Application-consistent backups: This approach focuses on capturing all the data related to an application at a specific point in time. The goal is to ensure that the backup mirrors the exact state of the application, including any ongoing transactions. This type of backup is particularly crucial for complex applications like databases, where data consistency is paramount.
- Application-centric backups: Conversely, application-centric backups go beyond just the data. They encompass the entire operational environment of an application, including configurations, settings, and dependencies. This approach is especially beneficial in Kubernetes environments where applications often have intricate setups with various interdependencies.
An easy way to implement these two practices is through Trilio. One of the key features of Trilio’s application-centric backup approach is that it can automatically detect, backup, and recover application data regardless of how it’s configured in the cluster. Your application could be set up via Helm, an Operator, grouped by labels, or a namespace. Trillio always does application-centric backups.
To implement application-consistent backups, Trilio has a hooks feature that enables the ability to run commands before and after backups and restores. This allows you to run commands that, for example, will flush a database or cache to disk before taking the backup.
Implement event-driven disaster recovery
Utilize a tool like Event-Driven Ansible to automate and execute unattended disaster recovery responses in Kubernetes environments. In this framework, specific event sources automatically trigger a decision-making process, leading to unattended actions, such as the recovery of an application to a remote cluster without the need for manual intervention. This setup ensures a proactive response to incidents and enhances the overall resilience of your Kubernetes environment by allowing for immediate, unattended reactions to operational disruptions.
If you are using Red Hat’s OpenShift platform across multiple clusters, you can benefit from automated data protection policies by integrating Red Hat’s Advanced Cluster Manager (RHACM) and Trilio. With policy-based enforcement, automate and trust that data protection is applied to applications and clusters as they are created. The result: you will always have a reliable backup if you need to restore.
Learn about a lead telecom firm solved K8s backup and recovery with Trilio
Final thoughts on Kubernetes Disaster Recovery
While offering a dynamic and robust environment for managing containerized applications, Kubernetes also presents unique challenges that require a well-thought-out DR strategy. Trilio emerges as a pivotal tool in this regard, offering solutions tailored to the specific needs of Kubernetes environments. Integrating a DR solution into your Kubernetes environment aims to ensure business continuity and maintain data integrity. By adopting the best practices and leveraging Trilio’s advanced features, you can protect against potential disruptions and maintain trust with your customers and stakeholders.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
