By Murali Balcha | October 25, 2022
Ransomware can devastate your reputation, customer loyalty, and overall business viability, making it one of the biggest and most dangerous threats that your organization faces today. Your best defense? Prevention. But it’s not that simple.
To be fully prepared for a ransomware attack, you need to follow all five steps laid out by the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework. There’s just one problem: Many ransomware protection solutions fall short when it comes to recovery.
Let’s take a look at their shortcomings, why recovery is so critical, and what to look for in a solution to help your organization be resilient against ransomware.
What Many Ransomware Protection Solutions Are Missing
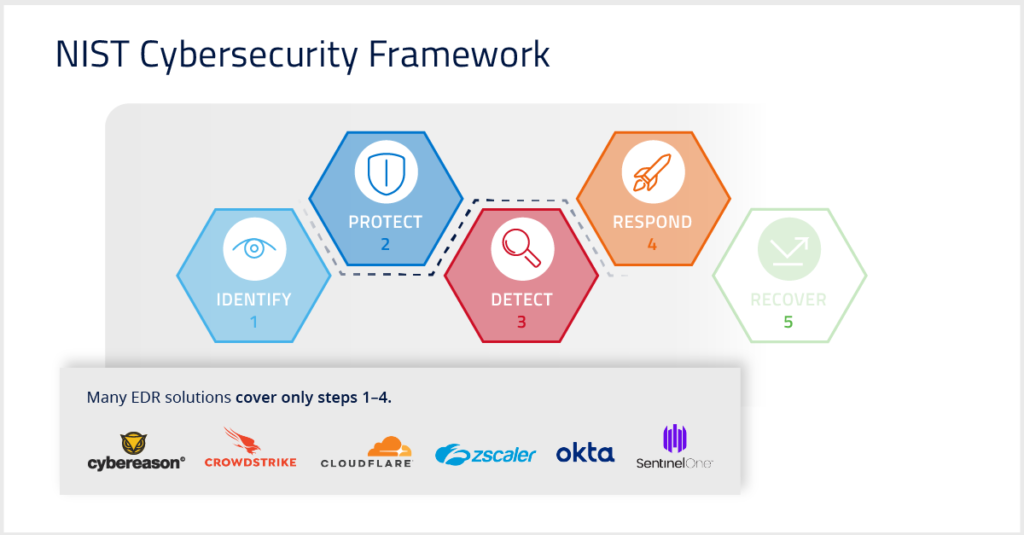
When it comes to ransomware protection, there are a lot of options out there. Many use an endpoint detection and response (EDR) system to pinpoint potential security issues as they occur and stop them from happening. And they work.
In fact, several EDR players offer a compelling solution to the first four steps in the NIST’s framework: identifying, protecting, detecting, and responding to ransomware attacks.
But it’s not always possible to stop an attack in real-time, especially because attackers are constantly exploring new vulnerabilities in the network. As these threats grow in severity and complexity, EDR solutions might miss one.
And it just takes one vulnerability to bring your organization to its knees.
So when an attacker finds that one vulnerability and your EDR solution can’t stop the attack, what do you do?
Why Recovery is Critical for Business Continuity after a Ransomware Attack
The best possible outcome is to return to the state before the ransomware attack happened—easier said than done, we know. However, with careful planning and implementation, it is possible.
The first step is to expand your defense to include the recovery phase of the Cybersecurity Framework. The best way to do that? Choose a data protection system that’s aligned with modern IT infrastructure. And not every vendor fits the bill.
To achieve resiliency against ransomware attacks, you need to think past the solution that merely backs up application data to a backup media and recovers them as needed. These systems are barely adequate to address the challenges of ransomware attacks.
Instead, your data protection system should be:
- Cloud-native
- Deployed and maintained using DevOps scripting
- Multi-cloud and multi-tenant aware
- Taking advantage of cloud storage, such as AWS S3 or compatible storage, for backup media
- Able to back up and recover using policy-driven plans
- Scalable to recover the entire organization in a matter of minutes
- Continuously tested
If your ransomware protection solution doesn’t meet these criteria, it doesn’t provide adequate protection, detection, and recovery from attacks. Thankfully, you have options.
Let’s take a look at the features your backup system needs to provide comprehensive ransomware protection for cloud-native applications, including recovery.
Learn more about Trilio’s Ransomware solution
Comprehensive Ransomware Protection & Recovery
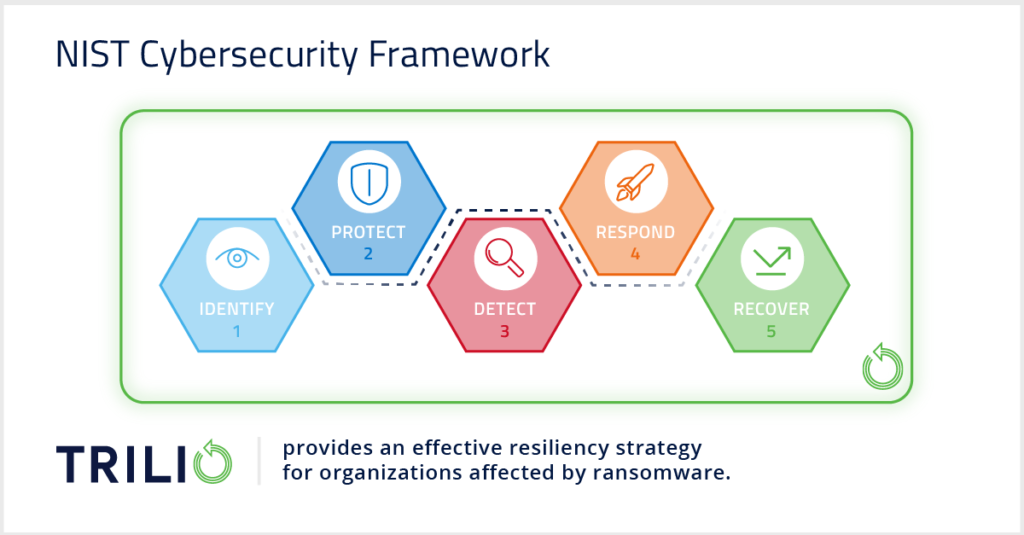
Effective, resilient solutions take inspiration and guidance from NIST’s Cybersecurity Framework. And unlike EDR solutions, the best options don’t stop at step four. Instead, they enhance all five steps, so you can achieve more resiliency against ransomware attacks.
Here’s how your backup solution can enhance each step of the Cybersecurity Framework.
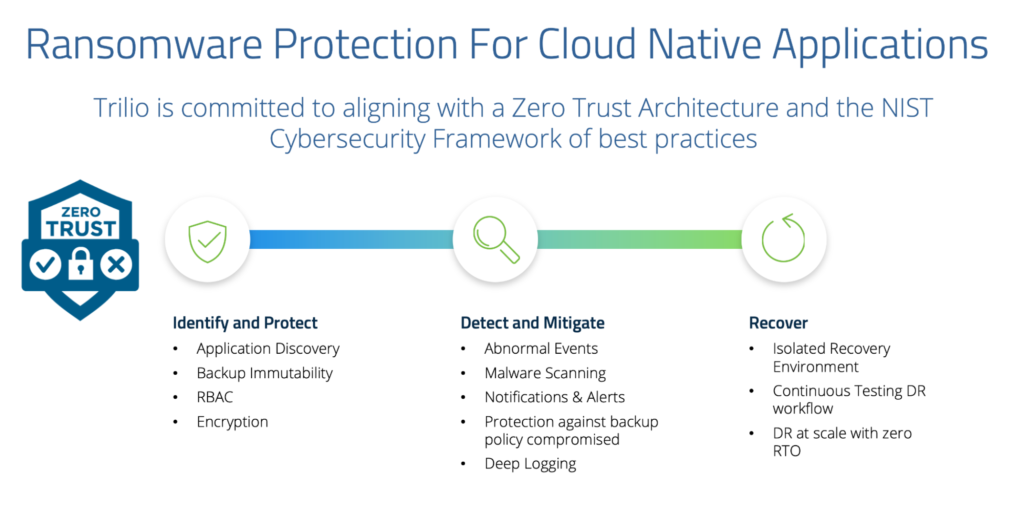
Steps 1 & 2: Identify and Protect
These steps involve identifying and protecting your critical resources, including hardware, software, business processes, and key personnel that are important to the business. When identifying these resources, don’t forget about the security of your applications, including backup software. Here’s why.
Backup systems and processes are critical components of your business because they not only contain business-critical data but also provide a roadmap to where sensitive application data is stored. And ransomware attackers can target both.
In fact, attackers may turn off or modify backup and retention policies to render backup systems useless for recovery.
If you use a traditional backup vendor, you’re vulnerable. Many use client/server-based architectures that provide a powerful administrative console to the server, offering a tempting target for attackers. So, what’s a better solution?
Choose a backup system that leverages cloud technologies, as they provide only a thin layer of abstraction to reduce the surface area of the attack. Less surface area = better protection.
Here are a few other things to look for in your backup system that help you identify and protect against ransomware.
1. Policy-Driven Data Protection
Traditional backup systems use an imperative approach instead of a declarative or policy-driven one. In other words, you need to identify and apply backup policies to every application manually. It’s time-consuming and prone to error.
However, a policy-driven approach applies backup policies to applications automatically. This ensures that applications comply with their recovery SLAs by continuously monitoring the policies and raising alerts to the administrator.
2. “Bring Your Own Keys” Encryption
Securely encrypting your backup data is vital to protect against data theft, a ransomware attack that includes stealing data for future criminal activities.
Make sure your ransomware protection platform uses the industry-standard LUKS encryption with tenant-provided keys, instead of merely relying on a storage-level secret key.
3. Immutable Backups
When ransomware attacks occur in distributed environments, it’s safe to assume that both the platform and its backup target are compromised. That’s because modern-day data protection architectures directly attach the backup target to the platform for scalability and performance reasons.
One way to address this is to choose a platform that supports immutable backups. These backups can never be deleted or modified from the platform after they’ve been created.
Trilio supports immutable backups leveraging the S3 object locking and versioning mechanism.
Steps 3 & 4: Detect and Mitigate
Your backup system can and should detect ransomware attacks—both active and dormant—early. These features can help.
1. Malware and Ransomware Scanning
Make sure to scan your application data continuously for malware detection using off-the-shelf scanners or the ones available on your platform. However, these scanners detect attacks best when they’re reviewing the most recent version of your application data.
With Trilio, the latest copy of your application data is readily available due to its new Continuous Restore feature. This always-on backup ensures that you can access—and scan—the most recent version of your application, no matter what storage, cloud, or distribution, so you can detect attacks before they start.
If you do detect ransomware, recovering to your last known good state is easy and fast.
2. Backup Anomalies
Cloud-native data protection platforms like Trilio can detect ransomware activity during their backup processes if they have an immutable backup feature. If an attacker makes any attempt to modify the backup, the data protection software will create a new version of it. When a new version is created, you’ll be alerted about suspicious activity.
Want to go further? You can also designate a few encrypted files to act as decoys and set up alerts for those files.
Because incremental backups are much smaller than full backups, an abnormal increase in backup size could be a sign of ransomware activity. If that happens, you can be alerted to the potential attack.
3. Protection Against Backup Policy Changes
Policy-based data protection is also essential to detect and mitigate ransomware attacks. In traditional data protection systems, attackers can disable scheduled backups or change retention policies to delete existing backups.
Cloud-native data protection platforms like Trilio rely on policy-based backups. So even if an attacker changes a backup plan, the policy engine can detect the change and raise proper alerts to the administrator.
Step 5: Recover
If you do get hit by a ransomware attack, the final step—recovery—is the most critical to getting your business back up and running. But the process isn’t as simple as just restoring from the backup.
That’s why your backup system’s performance and automation features matter. Here’s what makes recovery easier and faster.
1. Recovery at scale
Traditional backup systems specialize in backing up a large amount of data, but they’re not necessarily meant for recovery at scale. And depending on how extensive the attack was, you might need to recover at scale.
Cloud-native backup solutions scale with you, so you can recover what you need. If you choose Trilio, you can also take advantage of Continuous Restore, an always-on feature that stages the latest backup at a remote site. Since the application data is already staged, you can recover at scale faster and more easily.
2. Isolated Recovery Environment
Even after scanning your backup images, you can’t be sure they don’t have malware. To ensure your applications are 100% ransomware-free, you should build an isolated recovery environment. There, recovered applications are protected against external actors that might seek to trigger malware that was restored with applications.
But these isolated recovery environments can be hosted on any cloud, so they might differ from your production environment. To make sure they can fit those environments, they need to be transformed. That’s where your backup solution comes in.
Ransomware protection solutions like Trilio support various transformations that aid in restoring backup images to a wide range of cloud providers. Once you restore your applications, you can do additional scans before you move them into production.
3. Continuously Testing DR Workflow
Most backup systems can’t support regular recovery testing at scale. And 50% of organizations test annually or less frequently.
If you’re not testing your backups for recovery regularly, you probably don’t have a recovery plan. And your backup system might be to blame.
Many solutions don’t offer much automation capabilities. Even if they do, they require enormous computing and storage resources, a challenge for many organizations. So what do you do?
Find a cloud-native platform that helps you automate your recovery testing. For example, thanks to Trilio’s Continuous Restore feature, you can test your recovery workflow regularly on any cloud using DevOps processes, giving you confidence that your recovery at scale works when needed.
Make Sure Your Ransomware Protection Solution Includes Recovery
Full protection from ransomware attacks is more than just detecting the attack in real-time; it’s about being able to recover fast—with minimal downtime and data loss.
So make sure your ransomware protection solution doesn’t leave out recovery and can be automated, scalable, and native to your infrastructure, no matter what it is or how it changes.
If your platform falls short, check out Trilio. With its cloud-native, policy-driven, and DevOps-friendly functionality, you can rebound from ransomware attacks and achieve true resiliency.
Learn more about how TrilioVault for Kubernetes takes on ransomware or schedule a call with our K8s experts today.